Our computers serve as portals to a vast number of services and information that we utilize daily in the hyperconnected world of today.
However, with the use of modern technology, hackers and other malicious individuals can access and manage our computers from a distance without our knowledge or permission. This makes it very important to know how to check if someone is remotely accessing your computer.
I recently learned of an acquaintance who found out that someone had been remotely accessing her computer without her knowledge for weeks. She noted that her computer was operating slower than usual and that several strange programs were active in the background.
These kinds of incidents are frequent, so it’s critical to be alert to any indications that someone is spying on my computer remotely. This blog post will discuss how to tell if someone is remotely viewing your computer as well as security and private precautions you can take.
Tracking down remote access is not always easy, but it is not impossible either. If you suspect someone is remotely accessing your computer, take steps to gather evidence, such as taking screenshots or recording the behavior. You can also review your computer’s logs to see if there are any hints of remote access.
You can ask a computer security expert for help if you are unable to compile proof on your own. They can give you advice on how to protect your computer and assist you in figuring out whether someone is remotely accessing it.
These warning indicators point to potential remote computer access:
You may observe unusual network activity, such as a spike in network traffic or a slower internet connection if someone is remotely accessing your computer. Additionally, unfamiliar devices or unexpected links to your network may appear. If you see any suspicious behavior, you should immediately look into it.
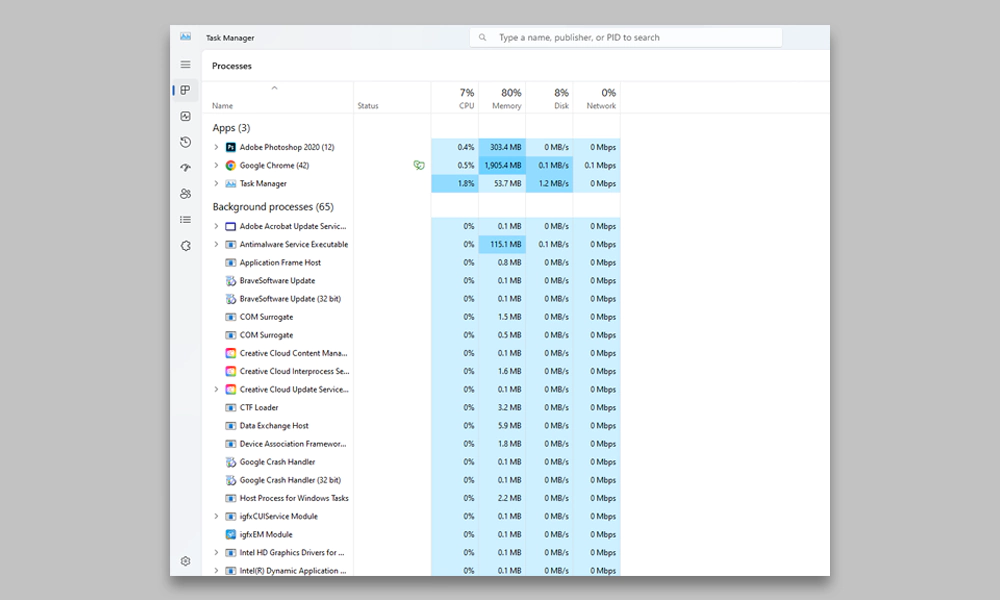
It is the best method for monitoring covert remote users. It is known as Task Manager on Windows computers and Activity Monitor on Mac computers.
Steps to use Task Manager in Windows to find remote access:
It may be an indication that someone is remotely controlling your computer if you observe odd mouse motions or clicks on it. This is so that someone else can operate your keyboard and mouse and use your computer without your awareness. Remote access makes this possible.

It’s obvious that someone is remotely accessing your computer if your webcam connected to your laptop is turned on without your awareness. They might be keeping an eye on you or hearing what you’re saying. If you’re not using your webcam or microphone, cover them to maintain your privacy.
It may indicate that someone is remotely accessing your computer if the computer is operating slower than normal. This is due to the fact that remote access makes use of your computer’s capabilities, which can make your system lag.
It may be a sign that someone is remotely accessing your computer if you observe unauthorized access to your accounts, including emails, social media, and banking. This is due to the possibility that remote access could enable someone to access your login information and log into your accounts without your knowledge.
Mac computers are known for their security features, but they are not immune to remote access. Here are some signs that your Mac might have been remotely accessed:
Strange pop-ups or messages on your Mac may indicate that someone is remotely accessing your computer if you spot them. These pop-ups or messages might be used to track your online behavior, steal confidential data, or take control of your machine.
It’s possible that someone loaded unfamiliar programs or files remotely if you find any unfamiliar files or programs on your Mac. These applications or files might be used to monitor your online behavior, steal confidential data, or take control of your machine.
It’s possible that someone has accessed your Mac online if the system preferences on your Mac have changed. It’s essential to check for any unapproved changes because remote access can be used to change your system settings without your knowledge.
If you want to prevent remote access to your computer, here are some steps you can take:
Disconnect from the internet right away if you think someone is directly accessing your computer. As a result, the remote user won’t be able to access your computer, giving you time to protect it.
Windows has a function called Remote Desktop that enables remote access to your computer. Disable remote access if you don’t require it to prevent unauthorized users from accessing your computer.
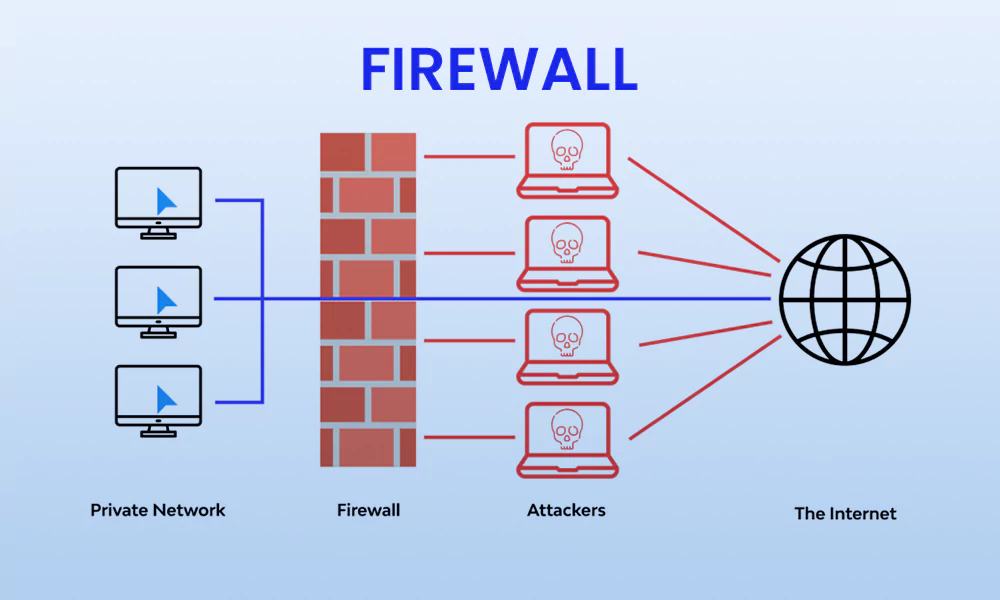
By blocking incoming connections, a firewall can help safeguard your machine from unauthorized entry. Make sure your firewall is set up correctly and enabled.

Your computer can be protected from malware that can be used to obtain remote access by using antivirus software. Ensure that your antivirus software is updated and loaded.
For all of your accounts, use secure passwords, and update them frequently. This will make it more challenging for someone to reach your computer remotely.
Your accounts are made more secure by using Two-factor authentication. Even if someone already has your login information, this will stop unauthorized access to your accounts.
We have covered many indicators to tell that someone is remotely accessing your computer in this blog. If you think someone is spying on your phone or remotely accessing your computer, you must be on the lookout and move right away.
We hope that you are now completely aware of how to tell if someone is remotely viewing your computer and how to safeguard yourself against such dangers.
