
In the age of digitalization, surfing the internet is a common practice, be it for shopping, booking tickets, or anything else. But if you are not careful, some malicious individuals might affect your security and privacy.
Mobile Proxy is an easy method employed by many people to mask their IP address and enhance their web security. But they are much more than simple address masking.
In this comprehensive guide, we are going to tell you all about mobile proxies and how they work.
In broad terms, mobile proxy can be equated to a group of proxy servers directing web traffic registered on an IP address through a cellular network, enhancing the user’s privacy and security.
Let’s have a look at how these work.
Whenever you surf the internet, the phone carrier services assign you a residential IP address. In some cases, your data security could be compromised if this IP address is leaked.
It is a gateway that masks your residential IP address or Virtual Private Network (VPN) and assigns your device an IP address.
Do You Know?:
The Mobile Proxy market appears to be very small in the US. And, it can be valued at 10-30 million dollars a year.
In simple terms, it creates an impression that the user is accessing the internet through a phone data network.
Since these proxies access phone networks from different countries and various network carriers, you can also access geo-restricted content through these proxies.
The question that arises is how mobile proxies can provide a phone network to any device. It functions using gateway software on any type of device to assign it a specific type of IP address.
This IP address belongs to a data network linked to a cell tower. Many IPs of the same network can connect through the same tower.
Due to this wide accessibility, any device equipped with hardware capable of reading a SIM card can be utilized to access a mobile proxy.
Also, since IPS are assigned by the network carrier, they are linked to all IP addresses registered to this carrier.
There are different types of it, for instance, 4G and 5G mobile proxies, rotating and dedicated proxies.

There are two primary approaches for creating one.
Once proxies are created, they are sold to individuals interested in utilizing them. Depending on the user’s demand, these proxies use IP addresses from 3G, 4G, or 5G devices.
Usually, 3G and 4G proxies are used in rural areas and are the most commonly used proxies.
Meanwhile, 5G proxies are used in metropolitan cities and offer faster internet speeds in comparison to 3G and 4G proxies.

Mobile proxies have significant features that make them stand out from other types of proxies. These differences can be attributed to how IP addresses are assigned to devices by carrier services.
Given the intricate design system of data networks, they cannot assign individually unique IP addresses to every device.
So, depending on the capacity of the mobile network, at times, the same IP address is assigned to hundreds of devices.
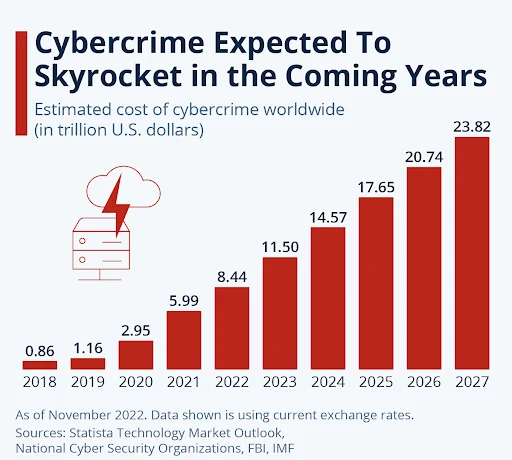
Statistics:
As you can see cybercrime is expected to skyrocket in the coming years. This led to the growing importance of using proxies that can safeguard IP addresses and prevent cybercrimes.
This practice of assigning the same IP address can be subjected to IPv4 shortage and the carrier-grade NAT technology (CGN) used to combat this data network issue.
Due to this shared address issue, websites cannot risk banning these IPs and cutting off their potential customers along with scammers posing as normal individuals.
Such discrepancy makes mobile IPs a favorable option utilized by online scammers.

Simply restricting all its users from accessing websites is not a viable option, as it would result in the loss of legitimate consumers. Due to this fact, scammers are most likely to use them and create disturbance for law-abiding citizens and their valuable assets.
Traditional anti-fraud protection such as IP reputation filtering does not provide adequate protection against these potential threats.
Therefore, modern protection techniques track scammers by engaging in IP analysis. IP analysis includes detections like velocity checks that calculate the time taken by the user to circumvent their searches.
When proxy detection inspects the probability of the user accessing the website through a proxy. These tools give an estimated assessment of the risk posed by the user.
Some security measures also combine additional features like biometric information to calculate the risk associated with a user. This assessment can also be aided with KYC verification.
The result of these assessments can sometimes constitute a permanent ban on individuals.
More importantly, such a direct approach only apprehends individuals found guilty of cybercrimes and does not restrict the general audience who have access to mobile proxies.
Interesting Fact:
In 2022, cybercrimes in the US made up to $10.3 billion in losses, according to this FBI Internet Crime report.
This strategy deters scammers who utilize them for malicious intent and ensures no additional expenditure to the company and a safe haven for its legitimate users.
Along with masking your IP address and protecting your privacy, mobile proxies also have other advantages.
You can easily utilize them to log in from multiple accounts, as the IP addresses differ for every connection.
Mobile Proxy is a versatile tool that safeguards your online security and provides you with peace of mind. But it is also necessary to remember the threat it poses in the form of scammers and how to circumvent them ensuring your safety.
Always remember to keep these points in mind especially when browsing through mobile proxies to ensure your data privacy.
