
Traditionally, business strategies involved having one team or department for physical security and a second group of IT professionals for cybersecurity. They were of equal importance but rigorously segregated with the group managing certain procedures and devices, while the other group managed computers and connections.
The traditional approach was based on the premise that even if safety was breached, sensitive data would remain safe, or vice versa. If digital data were breached, it would not affect substantial property protection.
Today, this type of safety management is outdated and ineffective due to many businesses and companies moving towards the installation of IoT devices and the use of smart technology.
Here you will get the guidelines regards choosing a reliable security system for commercial properties.
Many AI developments are now aimed at facilitating the creation of a connection between cyber and all types of safety and all professionals involved in a business’s safety strategy. Now the emphasis is on IT and logistical protection experts working together to reap the benefits of a converged business protection system.
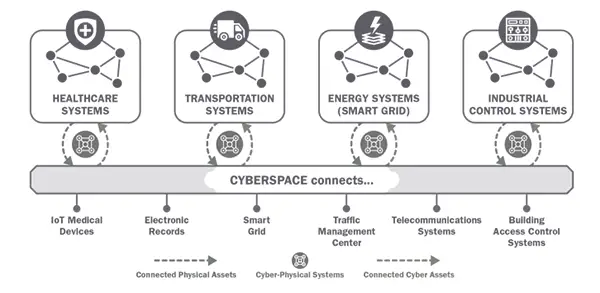
Interconnecting systems are challenging the traditional separation of cybersecurity and physical security as technology advances. What previously worked as individual siloed systems is in contrast with the potential that technological interconnectivity provides. New technological advancements demand that teams work closely together for the new technology to be truly effective.
The skill sets of all safety team members are pooled to create operational procedures that respond to vulnerabilities that are often complex and to better protect companies from a variety of threats and risks. Protecting physical assets, installing video monitoring, and limiting access together with intrusion detection can now be managed jointly using a single interface.
With an increase in the use of interconnectivity technology, team convergence becomes more urgent as companies face increased potential surfaces of attack. Convergence requires all team members, regardless of their department, to share the common goal of protecting company assets.
Convergence is not simply combining two departments into one larger one. Convergence requires team members to establish objectives, policies, and procedures so that more than a unified department, the company benefits from a unified team that provides safety and manages risks, vulnerabilities, and threats together.
Yet, to enable protection teams to successfully converge, there are several important processes to enact.
Communication is the starting point for building protection convergence. All personnel must commit to convergence. Each department must be aware of the other department’s goals. Cybersecurity professionals may program smart devices per their priorities, which may, however, create difficulties for substantial safety teams. To build a converged system, one of management’s priorities should be planning how departments will share procedures, policies, and resources.
Business management should create a series of meetings and workshops where cybersecurity and substantial protection teams share what they know and how they operate existing systems. Both teams should collaborate in the creation of a shared database.
To unify privacy objectives and encourage cooperation, a management team needs to be created which combines leaders from both teams. The most experienced and authoritative members of both departments should be included rather than just selecting any department member. Experts recognized within their departments for their expertise by colleagues are ideal.
A converged leadership will be responsible for providing team members with tools and the policies and procedures involved in using these instruments. Communication needs to aid the differing teams in understanding not only their functions, but the functions of the other team involved. This will contribute to expanding the skill set of all members of the converged team and to building stronger collaboration among members.
Security leaders will need to formalize responsibilities and roles. Shared vulnerabilities for both cyber as well as substantial protection in linked assets will have to be identified, assessed, and then analyzed to indicate shared solutions.
The principal benefit of combining substantial and cyber protection teams is that both teams can consult useful data from both types of devices and procedures, especially how they relate to one another. Creating a shared framework for collected data allows both sets of professionals to analyze a greater and more detailed collection of information.
The creation of a shared framework will permit both teams to contribute data into a central database that was previously divided and segregated in one department or the other. This convergence of data can then be analyzed to obtain converged observations and insights useful to the entire system.
Cloud-based platforms for the convergence of data can be more effective than traditional systems. The combining of cybersecurity systems with material devices and systems on a cloud management platform will allow all converged team members to monitor systems remotely and make any adjustments, when necessary, from wherever they happen to be. This will also facilitate the use of unified processes and procedures.
Another attractive benefit is that companies are no longer required to install and protect expensive hardware on their premises when using the cloud. Everything can be stored on Cloud servers and managed remotely.
Further advantages include using the most recent tech tools, adding, removing, or scaling up or down resources quickly without interruption, but above all, it frees personnel to concentrate on specific strategic needs and tasks rather than wasting precious time and capabilities on constant monitoring.
With a shared framework for databases and remote cloud management, it will no longer be necessary for cyber and substantial protection teams to maintain separate databases. Historic data can be moved to the cloud where it can be easily accessed by all personnel, It and physical alike.
The point of creating a converged system is to communicate and share collected data using only a single platform. All devices such as keypad door access control systems, CCTV cameras, intrusion sensors, or access control systems will require programming to send all data to the shared management platform. This will permit any safety team member to examine all data from a single converged system. Combined data can produce greater insights into vulnerabilities and functions as a result.
Even as technology drives the need for convergence, there are still obstacles to overcome. Budget constraints can slow moving forward as can the dispersion of personnel and business locations. For employees that have worked for years in set roles, new responsibilities, and procedures can create confusion about individual roles within the security team. Skillset issues can also plague the initial period of change.
A cybersecurity vs. physical safety mentality is no longer efficacious for asset protection. Developing new procedures and company policies that combine the two kinds of skill sets involved will be necessary together with the creation of cross-data analysis.
To successfully develop a converged business security system, IT protection employees and physical protection team members will have to work together sharing data and expertise across the board to eliminate gaps in protection.
With smart technology, cyber systems and physical security are increasingly interdependent. Security convergence is no longer a futuristic concept, it is a present-day necessity.
