“It takes 20 years to build a reputation and a few minutes of cyber-incident to ruin it.”
– Stephane Nappo (VP Cybersecurity Director at Group SEB)
We have just stepped into the third month of the year and already thousands of security breaches have been reported. Though there is no certain number, the estimates suggest that the frequency of cybercrimes will only continue to rise, and its global cost will reach $10.5 trillion by the end of this year. (Electric: High Profile Company Data Breach)
Since businesses often become the prime target for cyberattacks, such statistics raise huge concerns for them, serving as a wake-up call to implement robust security measures and threat intelligence systems.
In this article, we will understand more about threat intelligence systems and also discuss some best practices for modern business. So, continue reading and learn how to safeguard your business from malicious digital attacks.
With the increasing frequency of sophisticated cyberattacks, businesses cannot passively wait for a security breach to initiate defensive actions, they must implement a proactive security approach. Threat intelligence can be understood as the collection, processing, and analysis of data to identify a potential offense, its target, motives, and methods.
In simple words, threat intelligence is using insights based on evidence, to understand the context, indicators, mechanism, and action-oriented advice on existing and emerging risks. By helping in everything from understanding attack mechanisms to predicting possible incidents, it provides the opportunity to strengthen the security stance of businesses.
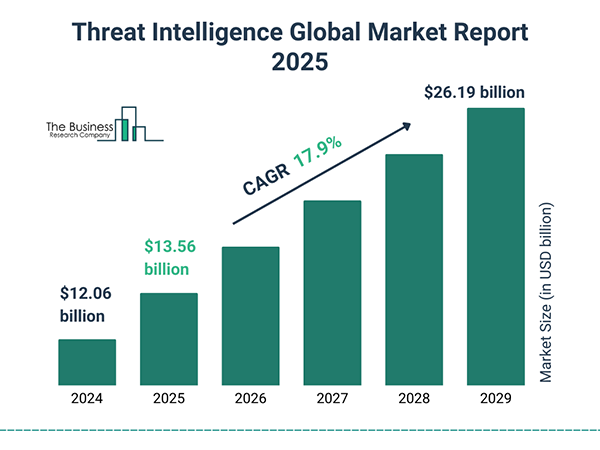
Since it proves to be a vital tool for modern businesses, the threat intelligence market is on the rise and is projected to grow at a CAGR of 17.9% and reach $26.19 billion by 2029.
Threat intelligence plays a significant role in the overall security posture of businesses. It delivers useful information to security professionals that helps them anticipate attacks to completely stop them or manage them at an earlier stage to minimize damages. Some of its major roles are listed below:
These points prove that the importance of threat intelligence systems for modern businesses cannot be overstated.
Now that we know the meaning and role of threat intelligence for modern businesses, here are some best practices that will help you effectively implement and manage this anticipatory approach in your business:
Defining clear objectives, goals, and expectations is essential for proficiently managing your threat intelligence. You can utilize an inventory of digital and network assets to determine and prepare for potential adversaries.
Numerous cyber threat intelligence tools and platforms are available in the market, and each offers a unique set of features. Choose tools that serve the right purposes and integrate seamlessly with your system.
Also, the cybersecurity needs for a system escalate with the growth of businesses, therefore select flexible and easily scalable tools.
Fighting against cyberattacks is a shared responsibility, do not hesitate to involve different teams, stakeholders, and organizations to enhance the security systems.
In addition to this, participating in information-sharing community and industry forums will help you stay informed about emerging concerns and their solutions, providing a comprehensive view of threat intelligence.
Security teams and hired staff play an important part in maintaining the effectiveness of security measures. Focus on both theoretical and practical aspects when training your security staff. Cover important topics like threat modeling, intelligence gathering, analysis, and dissemination and how to use frameworks like MITRE ATT&CK.
DO YOU KNOW?
A cyberattack happens every 39 seconds.
As said before, waiting to be struck by a cyberattack before taking any action can result in severe consequences and significantly increase the dangers of the attack.
Maintain a proactive approach by focusing on identifying potential breaches before they even occur, understanding threat actor tactics, and leveraging intelligence for effective threat management.
Setting up cybersecurity measures is not where the work ends, continuously monitoring their performance and evaluating their effectiveness is equally important to tackle the constantly-evolving cyberattacks.
Regularly accessing the key performance indicators (KPIs) will help you identify the areas of improvement and make changes accordingly to further enhance the security posture. Also, establish a security feedback loop to gather relevant insights from security operations, incident response and other relevant teams.
The increase in the frequency and sophistication of cyberattacks in the past few years is quite evident. Since businesses often become a primary target for vicious cybercrimes, the need for proactive threat management systems for modern businesses is now more than ever.
Threat intelligence management plays a significant role in this, as it actively collects, processes, and analyzes data to identify potential hazards and gathers all the important information related to them.
Integrating the best practices shared in this article in your modern business will enable you to effectively manage threat intelligence systems and enhance the overall security posture of your organization.
So, if you haven’t already, introduce threat intelligence in your business today and safeguard it from malicious cyberattacks!
