If you are not completely confused by quantum mechanics, you do not understand it -John Wheeler
Do you know about quantum computing? According to ResearchGate, “Quantum Computing is a fascinating new research area at the intersection of computer, science, mathematics, and physics. This branch studies how to harness some of the strange aspects of quantum physics for use in computer science.”
It can solve complex problems without any issues and is far more effective than traditional computers. It’s like straight out often Matrix kind of thing but doesn’t involve any action or something.
Furthermore, it’s also been proven that it can influence digital safety. But how? Well, I’m going to tell you why quantum computing could redefine cybersecurity and encryption.
Quantum computing is based on 4 principles taken from quantum mechanics. This includes:
These are the mechanics used in quantum computing, and each one of them is essential and holds a significant value. In the next heading, I’ll mention how it affects cybersecurity.
People are not understanding this, but quantum computing is affecting cybersecurity negatively. Yes, you heard it right. It can easily break through current encryption methods such as the RSA, 3DES, AES, and more.
This is possible because quantum computing can factor advanced prime numbers faster than traditional ones. This way it can breach and get past security protocols, but there’s a catch. So far, the current quantum computers are not powerful enough to do this task on a large scale.
There are also benefits of quantum computing, like it is bringing unexpected advancements in secure communication. With the help of different programs, for instance, Shor’s algorithm can solve complicated problems in an instant. Several other advantages are mentioned in the infographic below.
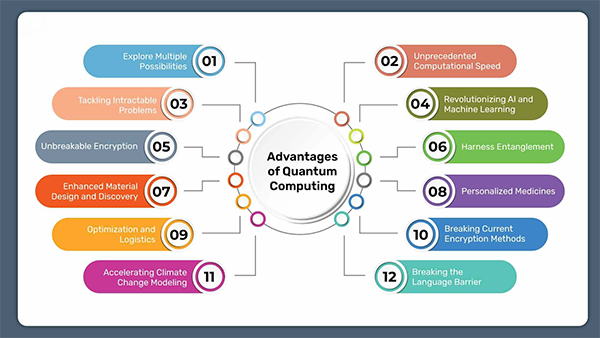
You might’ve realized that it is no less than a double-edged sword, while it can create unbreakable encryption it can break the current ones that are crucial for securing online information.
Even tho quantum computing isn’t in practice at the moment, it has been determined that several hackers have started storing encrypted data which can decrypted later when quantum computing is used.
According to a survey done by KPMG, 78% of U.S. and 60% of Canadian organizations are expecting quantum computing to come by 2030, but they are worried about the risks and its impact on encryption breaking.
Quantum computing can significantly improve cybersecurity. Here’s how:
As mentioned earlier, it can easily crack the current encryption system, posing a major threat to its advancement. But can it be solved? Researchers are creating post-quantum cryptography (PQC) which will repel attacks coming from quantum computing.
Now, what’s the future of quantum computing? Well, it will revolutionize everything, and sectors like finance, healthcare, scientific research, and more are going to greatly benefit from it.
It can help discover previously unknown drugs that can cure diseases, and a financial institution can analyze several portfolios at once and make an informed decision. Since it can solve any complexity in an instant, it will help with innovation creating a better future.
Quantum computing is still a work in progress, but soon enough it will change everything and will be treated as a miracle.
DID YOU KNOW?
David Deutsch invented quantum computing in 1985. In 1994 Peter Shor stated that quantum algorithms can break several encryption including RSA!
Quantum computing is the future of cybersecurity. It can make it invincible and impossible to break, resulting in the best secure system. But it can be used against the current encryption system, which won’t be good.
Developers are coming up with an enhanced solution to neutralize this threat and make it the best possible system that will shape our future. It will assist us with staging ahead of any emerging threat and counter it.
