Cryptography has endless applications, from secret messages in wars to securing modern communication. If you plan to decipher the code Zpv Bsf Bxftpnf while gaining insight into this intriguing world, you have arrived at the right place.
Whether you are a beginner or a coding enthusiast, decoding Zpv Bsf Bxftpnf will give you a glimpse of this secret communication world. Through this article, you can learn about the types of codes and ciphers, their usage in the real world, and their importance.
Step into the world of encrypted codes and get ready to uncover the mystery behind these secure communication texts.
If you are eager to decipher the code Zpv Bsf Bxftpnf, you are in the right place!
Used in various fields, codes and ciphers are quite in the limelight these days. Many technical jargon have become the new internet sensation in the landscape of secret communication. This type of confidential messaging is also known as cryptography.
Although codes and ciphers are both types of encrypted messages, their working is different from one another. A code is a method of changing the entire word or phrase into completely something else. For example, “mission complete” can be coded as “over and out” or “president” can be coded as “eagle”.
Whereas ciphers use a technique to change or rearrange the order of alphabets to present the original message as a random string of characters. For example, A = Z, B = Y, and so on.
One such popular cipher text is Zpv Bsf Bxftpnf. Moving forward, let us decipher the code, and learn more about cryptography, its types, and its uses in different domains.
To decipher Zpv Bsf Bxftpnf, we will be using the Caesar Cipher methodology. Used by Julius Caesar in 58 BC to pass his military messages without getting decoded, the Caesar cipher process involves shifting the characters by a certain number of letters. For example, a shift of +1 in “A” will be written as “B” or a shift of -1 in “B” will be written as “A”.
Similarly, let us try to decipher Zpv Bsf Bxftpnf in words. By applying a shift of -1 on each character, the code goes like this:
Z ➡ Y
P ➡ O
V ➡ U
B ➡ A
S ➡ R
F ➡ E
B ➡ A
X ➡ W
F ➡ E
T ➡ S
P ➡ O
N ➡ M
F ➡ E
As we can see, the code for Zpv Bsf Bxftpnf is “you are awesome”. The message conveys a tone of appreciation or praise. It can be affirmed that coded texts can also be used for personal messaging or even in games or puzzles.
To understand the different types of codes and ciphers, we first need to dive into the history of cryptography. Breaking down the word, “crypto” stands for hidden, and “graphy” means writing, and its emergence dates back to a thousand years ago.
Converting plain text into pictorial formats or rearranging the characters of the message was first seen in Egyptian hieroglyphs. The first attestation of a cryptographic message was found in 1900.
Furthermore, this coding language has seen many advancements over the years. The major two types of methods used to convey a confidential piece of information are either codes or ciphers.
Let us explore more about the various types of codes and ciphers.
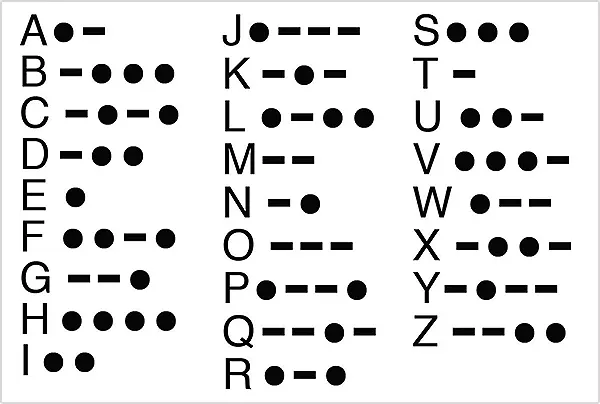
Named after Samuel Morse, it is a method in which the encoded texts are written using dots, dashes, and spaces. Since this method lacked coding signals for certain letters, it was further improved by Morse’s assistant and partner, which later came to be known as the International Morse Code.

An important concept in digital electronics, this coding pattern involves two digits, 0 and 1. This is a primary language in any computing system. Organized into segments like bits or bytes, each code represents a piece of information in the world of computer communication.

A not-so-commonly used coding language, this type includes encrypted messages that look like musical sheets. It is an algorithm that assigns different notes to each alphabet so that nobody can decode the message other than the ones who know musical notes.
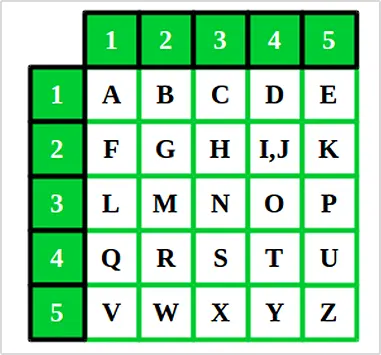
Better known as Polybius square, in this method the alphabets are written in a grid, mainly a 5*5 box, having all the alphabets assigned a number. To decipher the message, you need to check the coordinates of the box. For example, the letter “S” will be coded as 43.
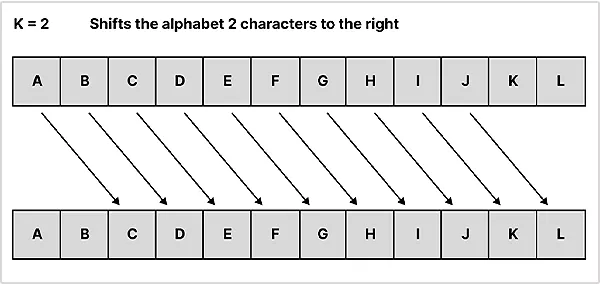
As noted earlier, this cipher technique was used by Julius Caesar to transmit military messages to his generals or army men. You simply need to set a specific count of shifts for the alphabet in the coded text, and you are done.
For example, with a shift of 2 keys for each character, “hello” will be written as “jgnnq”.

Found mostly in ancient Roman times, this is a secret code of its own. Every word or syllable is depicted by a picture. Hieroglyph means sacred carving, which in Greek means “god’s words”. This type of cryptographic message was particularly found on ancient Egyptian monuments.
Various other forms of codes or cipher techniques are used to deliver secret or coded texts. Transmitting information using these methods can help maintain the confidentiality and integrity of the message. In the following section, we will understand the importance of cryptography.
Want to keep your data protected and coded? Cryptography is your answer. Commonly used in ancient communications, in today’s era it is primarily used in cybersecurity departments. To maintain the privacy of the information transferred, this technique is used by both, large firms and local individuals.
Moving ahead, let us understand the importance of cryptography.
With the world shifting toward everything digital, cryptology has become an integral layer of defense used by many major businesses. It has now set off to be the foundation of modern security systems.
If you are a coding enthusiast who plans to decipher the meaning of Zpv Bsf Bxftpnf in words. Also, if you are passionate about similar cryptic codes like U231748506 and 6463276197 you may want to explore and understand more about the application of cryptographic messages.
Some key uses of cryptology are discussed below.
Beyond digital use, this method is used by many individuals or common messengers to convey their intentions in a fun way.
In today’s technology-driven world, the field of coding language will continue to step towards various advancements. Any business or any individual can safeguard its personal information from unauthorized access.
This article has been delivered to decipher the code Zpv Bsf Bxftpnf and to give you a comprehensive overview of cryptology, its uses, and its importance. If you have cracked the code for Zpv Bsf Bxftpnf, well done! Your journey has just begun. Who knows what mysterious code you come across next?
The code Zpv Bsf Bxftpnf means “you are awesome” in normal language.
Yes, any general or conversation text can be written in a similar format using cryptography.
There is no explicit meaning of 6463276197. This code is yet to be deciphered.
By learning cryptography, one can have widely open career opportunities, or you can also learn to evoke curiosity and engagement among your peers.
