KEY TAKEAWAYS
- DAM centralises files with secure access controls to reduce data loss.
- Built-in version control and backups protect against errors and accidents.
- Strong security features in DAM defend against cyber threats effectively.
- Compliance tools in DAM safeguard brand reputation and legal requirements.
According to IBM’s 2024 Cost of a Data Breach Report, the average data breach is now a record global cost of $4.88 million. This should make organizations take notice of the serious financial and operational costs to their company when their critical data is eventually lost or compromised.
There is a solution that is built for not just storing critical documents but also securing and managing, and protecting that information to limit, control, and track access. It provides backup restoration as needed for internal accidents and external security incidents.
In this article, I will explain how this technology helps to mitigate risk, increase protection of data, and provide continuity to the enterprise.
When files are spread across different locations, the risk of losing or accidentally deleting them becomes higher. A digital asset management system keeps everything in one secure place, helping reduce that risk.
You also gain the advantage of flexible permissions, allowing you to control who can view, edit, and share content across teams. When combined with strong security features, like multi-factor authentication, single sign-on, and encrypted connections, these systems make it harder for intruders to gain access or exploit sensitive company information.
Teams can easily overwrite files by mistake or lose track of the most up-to-date version. DAM platforms solve this with built-in version control, giving you a full history of changes for review. If errors happen, you can restore earlier versions quickly without disrupting workflows.
Backup features add extra security, protecting files from hardware failures, accidental deletions, or even user mistakes. These protections guarantee that your assets stay secure, never disappear unexpectedly, and are always accessible whenever your organization requires them.
Cyber threats affect organisations of all sizes. Phishing emails, ransomware attacks, and unauthorized logins can pose serious threats to data security. A DAM defends against these by combining access controls, encryption, and approval workflows that limit exposure.
Sensitive files cannot progress without proper checks in place, adding an extra layer of protection and reducing risks. Audit trails also record every action, making it easier to spot unusual activity, trace responsibility, and respond effectively before bigger problems develop across your network. Below, you can see some other protective measures.
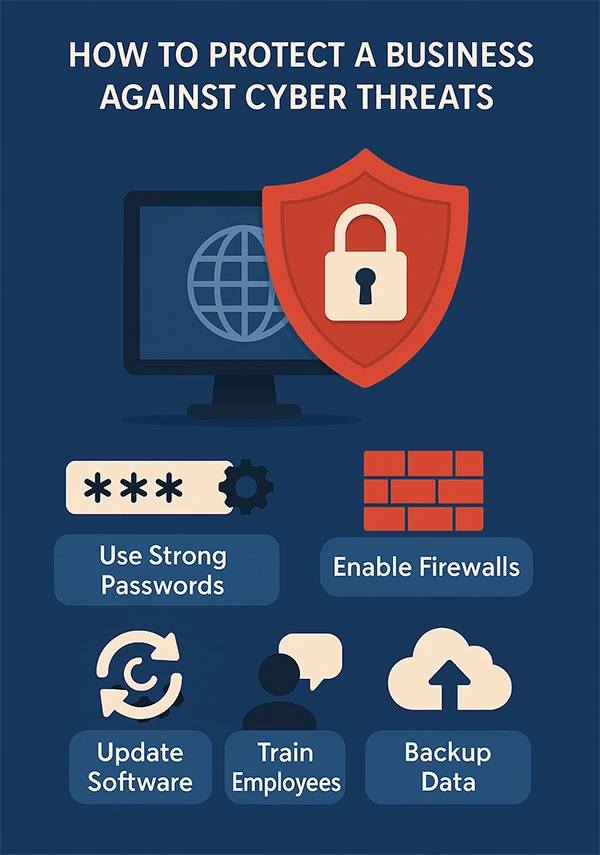
File loss goes beyond wasted time, if an outdated or unapproved asset is used, it can damage your brand’s reputation and erode customer trust. DAM platforms help by setting expiry dates, embargo rules, and alerts that block the wrong files from being used across campaigns.
Rights and consent form management also protects you legally, ensuring your organisation doesn’t breach copyright or data laws while supporting stronger compliance with industry standards and internal policies.
Even with strong defences, no system is completely risk-free. The most important factor is how fast you recover and return to normal operations. DAM solutions include recovery tools and duplicate detection to speed up response and minimise downtime.
If a file gets corrupted or deleted, you can restore it instantly without searching through devices, inboxes, or fragmented backups. This keeps your operations running smoothly, protects productivity, and ensures critical projects continue even during unexpected setbacks or technical issues.
Relying on scattered storage exposes you to risks that harm productivity and trust. A digital asset management platform offers secure storage, access management, and recovery tools that protect your assets against data loss and cyber threats. Implementing a DAM system means choosing a smarter, more secure way to manage and safeguard your organization’s most important files.
A DAM avoids data loss via centralisation, backups, versioning, and permission settings that prevent deleting files either accidentally or maliciously.
Yes, a DAM can use encryption, access controls, audit trails, and approval workflows to mitigate exposure to cyber threats to sensitive files.
A DAM can impose expiry dates, consent and usage management by ensuring only approved assets are used, while complying with legal & industry compliance requirements.
